12 Analysis view
View reports and assist in risk evaluation of the project.
The analysis view contains a number of reports, some of them interactive, that are useful in preparing the longlist and shortlist during the Risk Evaluation stage. Tabs along the bottom give access to various tools and reports.
12.1 Failures and vulnerabilities
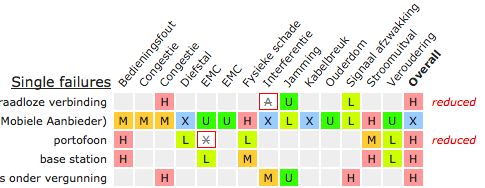
This table shows a condensed overview of all vulnerabilities against the single failures and common cause failures. It allows you to quickly visualise the most critical nodes.
This table is interactive. You can:
- ignore a vulnerability, by clicking it. The square will colour white with a red border to indicate its status. If ignoring this vulnerability would cause the overall vulnerability level to change, the marked reduced appears on the right hand side of the row.
- include an ignored vulnerability, by clicking it.
- include all ignored vulnerabilities, using the “clear exclusions” button.
- show all quick wins automatically, by clicking the “show Quick Wins” button.
Quick wins are those vulnerabilities that by themselves determine the overall vulnerability level. Reducing that vulnerability would immediately reduce the overall level. Quick wins are therefore a useful priority for risk treatment.
12.2 Assessments by level
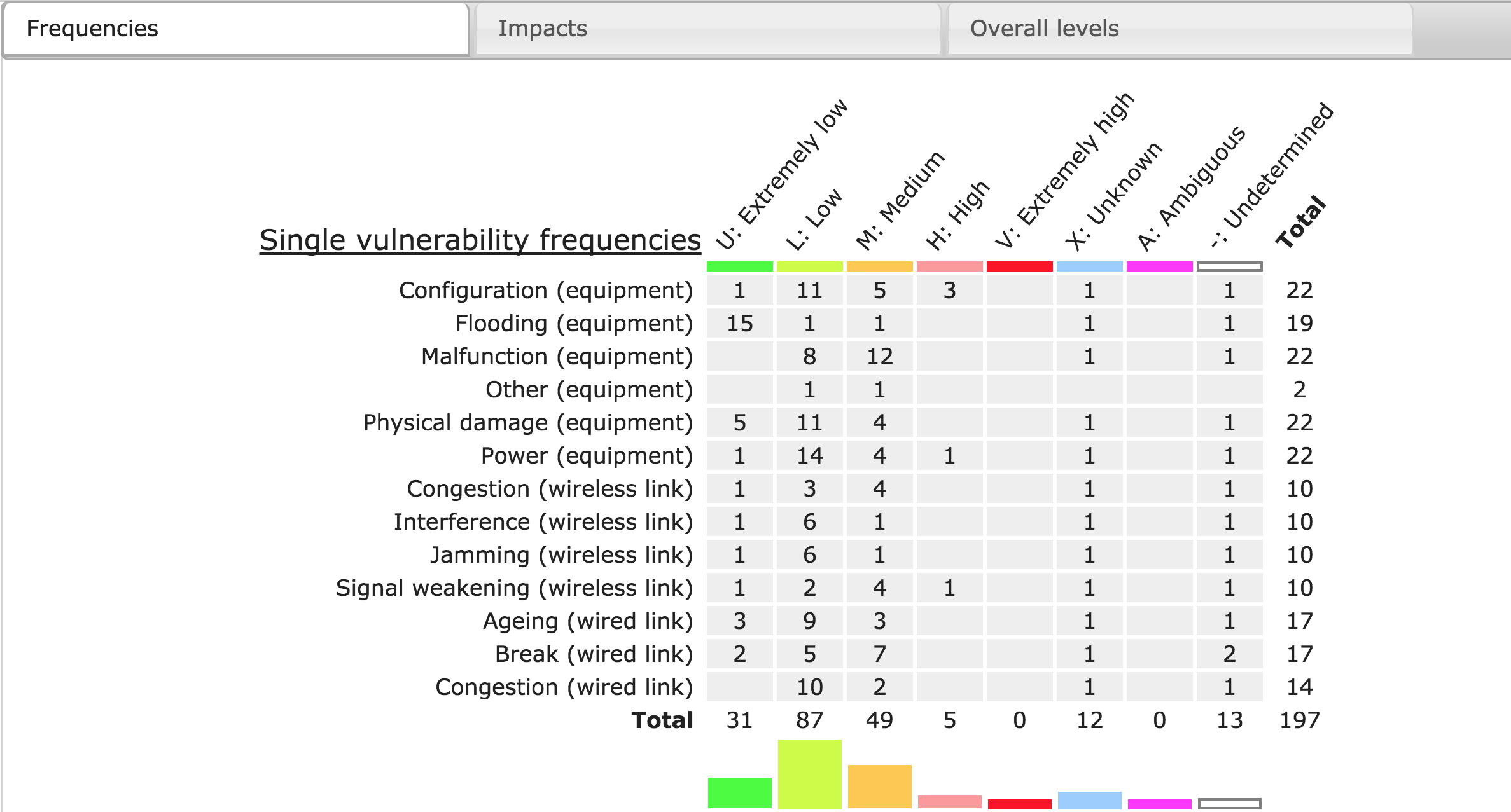
These tables show an overview of all assessments. The Frequencies table shows how often each frequency was assigned in the Single Failure and Common Cause Failures stage, including the totals per frequency class and per node class (both as numbers and visually). The Impacts table does the same for impact assignments. The last table shows the combined vulnerability levels. All tables are informational.
12.3 Node counts
This table shows the number of occurrence for each node type, for each service and for the project as a whole. It is purely informational.
12.4 Checklist reports
Two overviews help determine how useful the checklists were, and what vulnerabilities were added during the Single Failures stage.
Removed vulnerabilities: lists all vulnerabilities that are present in the checklist for a component, but not on the component itself. Section Adding and removing vulnerabilities warned that vulnerabilities should only be removed when physically impossible. This report helps to verify this.
Custom vulnerabilities: lists all vulnerabilities that are present for a component, but not in its corresponding checklists. This is purely informational.
12.5 Longlist
This longlist view selects all single and common cause vulnerabilities above a chosen level. This can serve as a good first attempt at the longlist in Stage 4. Often, the list of all High vulnerabilities together with all Unknown and Ambiguous vulnerabilities can be used as the longlist.

