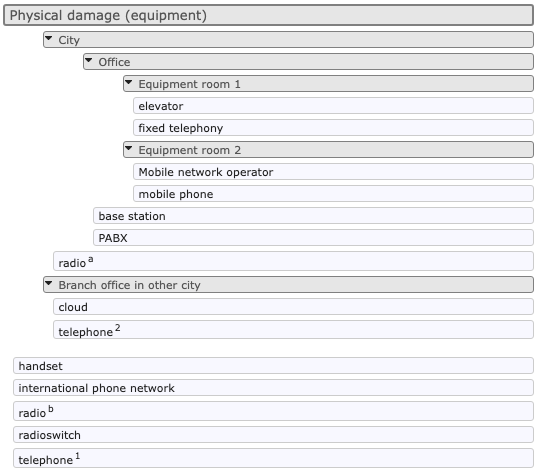

All nodes subject to the vulnerability are listed to the right the table of vulnerability assessments. Initially all the nodes as shown in a single list, sorted by label and by name. There are two mechanisms to sort nodes into clusters: by using the menus or by 'drag and drop'. Either way you can group nodes into clusters, and rearrange nodes and clusters in a nested structure.
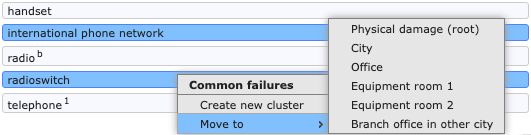
Each node is shown using a simple white row. You can select one or more nodes, and use the popup menu to move the selection into a new or existing cluster.
You can:
To move all currently selected nodes, use the right mouse button to call up the popup menu.
Note that after moving nodes, any clusters with less than two nodes or subclusters remaining will automatically be cleaned up.
Each cluster has a grey header; the nodes in that cluster are listed below the header, after the subclusters (if any). Unlike nodes, cluster headers cannot be selected.
Open or close the cluster, by clicking the header (either on the triangle or to the right of the title). Rename the cluster by clicking its title. Note that the root cluster cannot be closed nor renamed; it always has the same name as the vulnerability itself.
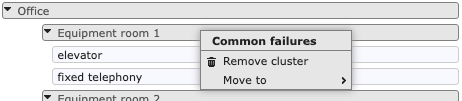
To move or remove a cluster, use the right mouse button to call up the popup menu.
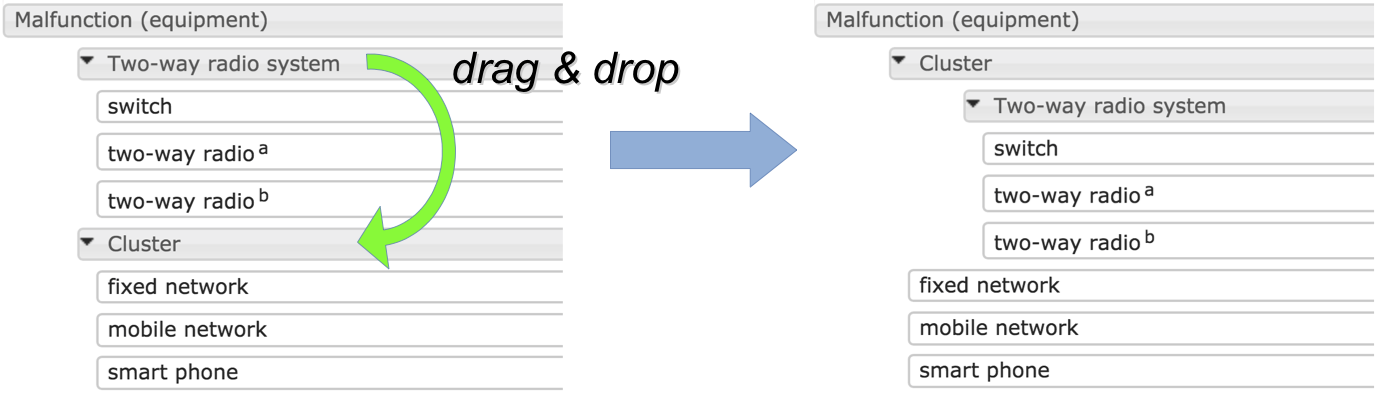
Nodes and clusters can also be arranged and rearranged using 'drag and drop'. Clusters are dragged by dragging their header row. While dragging a node or cluster, all possible drop targets light up in pale green. You can first select a number of nodes, then drag them collectively. You can:
create a new subcluster, by dragging a node onto another node. Both nodes must belong to the same cluster, and will be combined into a new subcluster thereof. See the picture below. The new cluster will get a default name, and the two nodes and all other selected nodes will be shown beneath it, indented from the left margin.
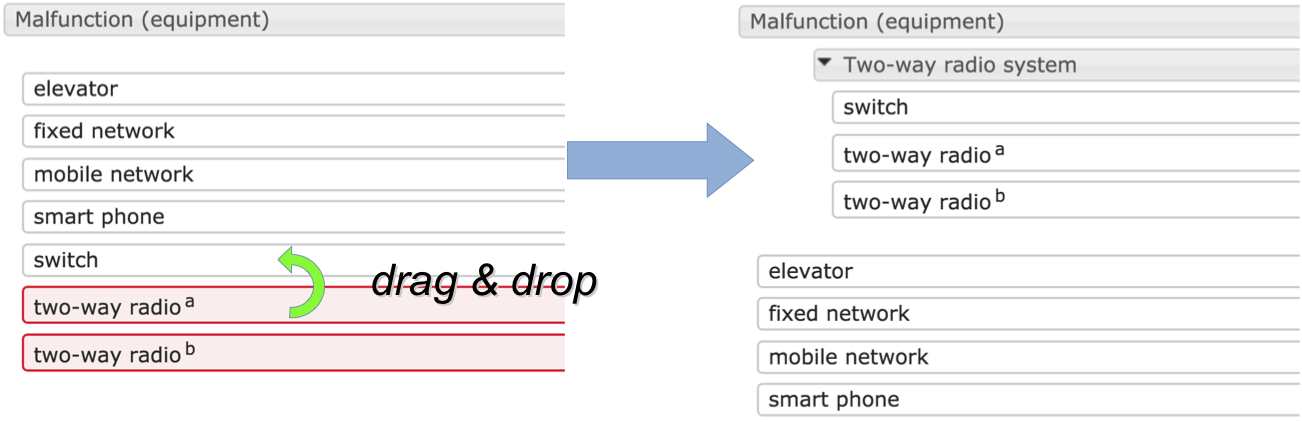
move a node or selection, by dragging it onto the header of any cluster.
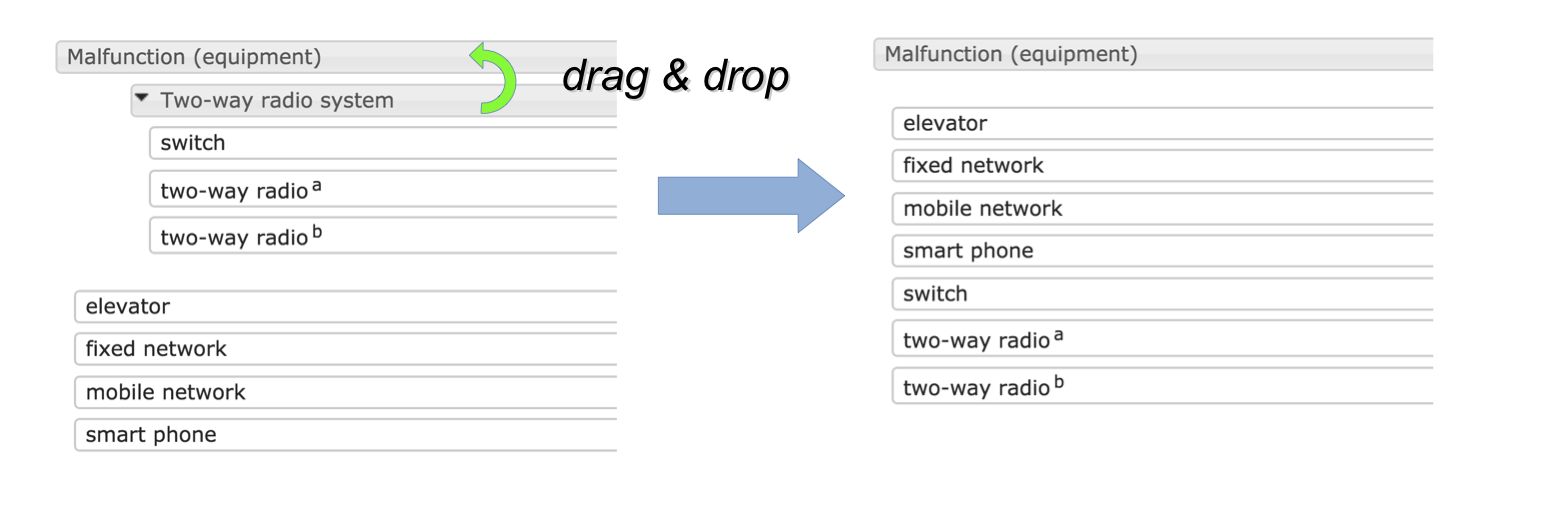
remove up a cluster (dissolve it), by dragging the cluster header onto the header of its parent, as illustrated below. The nodes in the cluster will be merged with the parent cluster. When a group is removed, the assessment for that group will be lost.
move a cluster, by dragging its header onto the header of any cluster except its direct parent. The cluster will become a subcluster of the cluster on which it was dropped, as illustrated: